Break-glass accounts with Conditional Access Policies that Enforce MFA
You will want to ensure that you have added appropriate users to the Emergency Access group that is created as part of the baseline to not lock yourself out of the Microsoft tenant. At a minimum, this should be a user with Global Admin permissions.
MFA registration and usage shall periodically be reviewed
MFA registration should periodically be reviewed to ensure that there are no gaps or misconfigurations in deployment. MFA can be monitored natively within Azure Active Directory or with 3rd party tools.
Viewing Authentication Activity in Entra ID requires an Entra ID P1 license which can be purchased standalone or through the following common plans:
- Microsoft 365 Business Premium
- EMS + E3 or EMS + E5
- Microsoft 365 E3
- Microsoft 365 E5
MFA reports can also be derived from PowerShell which does not require an Entra ID P1 license and can be used with any Microsoft licensing model.
- To view the authentication activity, refer to the article Authentication Methods Activity on Microsoft Learn.
- For details on reviewing Microsoft Entra multifactor authentication events, see the article Use the sign-ins report to review Microsoft Entra multifactor authentication events on Microsoft Learn.
- To learn how to list credential user registration details using the Microsoft Graph API, check out the article List credentialUserRegistrationDetails on Microsoft Learn.
Guest user access shall be restricted
Ensure that only users with specific privileges can invite guest users to the tenant and that invites can only be sent to specific external domains. Ensure that guest users have limited access to Entra ID directory objects and that they are required to use MFA.
Guest invites should only be allowed to specific external domains that have been authorized by the agency for legitimate business purposes. A formal process should be put into place to submit for new guest user access. Guest Access should be reviewed on a quarterly basis for proper access control standards.
For more details on how to manage guest invites, you can refer to the Allow or block invites to specific organizations documentation on Microsoft Learn.
- Use the collaboration settings for external users who are not using Azure AD.
- Use cross-tenant access settings for external users in another Azure AD environment.
The number of users with highly privileged roles shall be limited
Global Administrator is the highest privileged role in Azure AD because it provides unfettered access to the tenant.
Therefore, if a user’s credentials with these permissions were to be compromised, it would present grave risks to the security of the tenant. Limit the number of users that are assigned the role of Global Administrator. Assign users to finer-grained administrative roles that they need to perform their duties instead of being assigned the Global Administrator role. A minimum of two users and a maximum of four users SHALL be provisioned with the Global Administrator role.
- In the Azure Portal
- Navigate to “Microsoft Entra ID”.
- Select “Roles and administrators”.
- Select the Global administrator role.
- Under “Manage”, select “Assignments”.
- Validate that between two to four users are listed.
- For those who have Entra ID PIM, they will need to check both the Eligible assignments and Active assignments tabs. There should be a total of two to four users across both of these tabs (not individually).
- If any groups are listed, need to check how many users are members of each group and include that in the total count.
Highly privileged accounts shall be cloud-only
Assign user accounts that need to perform highly privileged tasks to cloud-only Azure AD accounts to minimize the collateral damage of an on-premises identity compromise. Users that need to be assigned to highly privileged Azure AD roles SHALL be provisioned cloud-only accounts that are separate from the on-premises directory or other federated identity providers.
- Follow these steps to review the administrative roles like Global Administrator
- Ensure that these accounts are cloud only
Azure AD Logs shall be collected
Azure AD logs should be a collected and periodically reviewed to detect any anomalies. Log information should be centralized in a SIEM tool, like Microsoft Sentinel, so that it can be audited and queried. Audit logs should be retained in a storage account for a minimum of 90 days.
Log events that can be collected are as follows:
AuditLogs, SignInLogs, RiskyUsers, UserRiskEvents, NonInteractiveUserSignInLogs, ServicePrincipalSignInLogs, ADFSSignInLogs, RiskyServicePrincipals, and ServicePrincipalRiskEvents.- Learn how to analyze sign-ins with the Azure AD sign-ins log on Microsoft Entra at Microsoft Learn.
- Follow this tutorial to route logs to a storage account and archive directory logs on Microsoft Entra at Microsoft Learn.
- Discover everything you want to know about Security and Audit logging in Office 365 from The Cloud Technologist.
- Explore the sign-in logs (preview) in Azure Active Directory on Microsoft Entra at Microsoft Learn.
- Learn how to connect Azure Active Directory data to Microsoft Sentinel at Microsoft Learn.
To retain Entra ID log data more than 7 days, an Entra ID P1 License is required. This license retains data for 30 days and is available to purchase standalone or as part of the following bundles:
- Microsoft 365 Business Premium
- EMS+E3/E5
- Microsoft 365 E3
- Microsoft 365 E5
Authorized Applications shall be configured for Single Sign-On
If available, all authorized applications should be configured for single sign-on to extend authentication security to 3rd party applications.
- The configuration settings will be application-specific, but all applications will be configured in the Enterprise application section of Azure AD. For detailed guidance, refer to the Enable single sign-on for an enterprise application documentation on Microsoft Entra at Microsoft Learn.
- For an example of single sign-on (SSO) integration, you can follow this tutorial on Azure Active Directory integration with Dropbox Business provided by Microsoft Entra at Microsoft Learn.
To configure Enterprise applications for SSO, an Azure AD P1 license is required. This can be purchased standalone or is available as part of the following bundles:
- Microsoft 365 Business Premium
- Microsoft 365 E3
- Microsoft 365 E5
- EMS+E3/E5
Inactive accounts shall be blocked or deleted
Deleting or blocking accounts that haven't been used for over 30 days helps prevent unauthorized use of inactive accounts. These accounts can be targets for attackers who are looking to find ways to access your data or move laterally throughout an organization without being noticed.
For detailed instructions on managing inactive user accounts, refer to the How to manage inactive user accounts in Entra ID documentation on Microsoft Entra at Microsoft Learn.
Blocking Sign-In
- Go to Microsoft admin portal
- Click “Users” > “Active Users”
- Select the account you want to block
- Click “Block sign-in” at underneath the account name
Users assigned highly privileged roles shall not have permanent permissions
Do not assign users to highly privileged roles using permanent active role assignments. Instead, assign users to eligible role assignments in a PAM/PIM system and provide an expiration period for active assignments requiring privileged users to reactivate their highly privileged roles upon expiration.
In Entra ID, you can leverage Privileged Identity Management (PIM) to set permanent and eligible assignments. There should be only one permanent assignment for your break-glass Global Admin account for the Global Administrator role. This user or service account is likely different in every Entra ID Tenant.
You can monitor the permanent and eligible assignments in Configuration Manager under the Azure > Privileged Identity Management > Policies and Rules Section (MS Graph/RoleManagement/Directory/RoleEligibility Schedules).
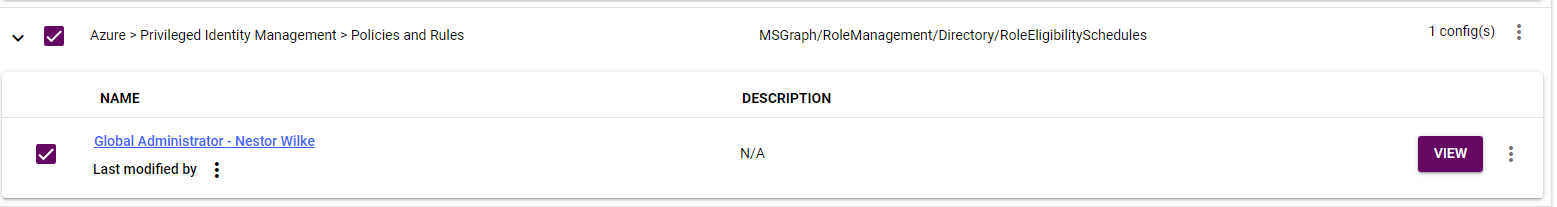
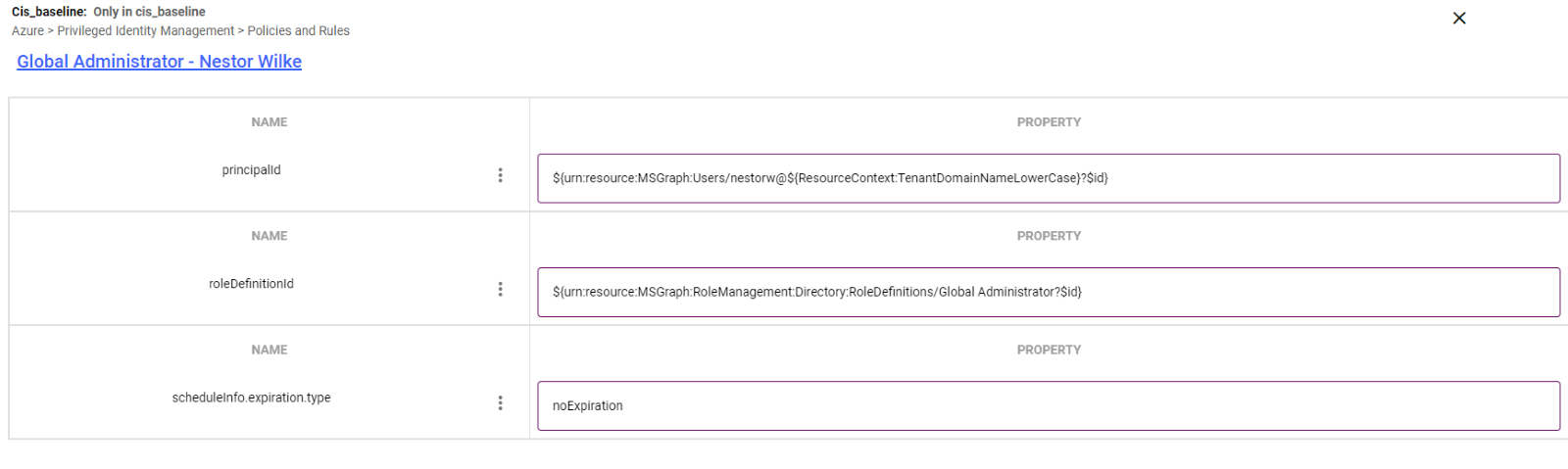
In the Entra Admin center.
- Entra AD Roles > Roles > Global Administrator
- Ensure All users with Global Admin role are in the eligible status except for one break glass account
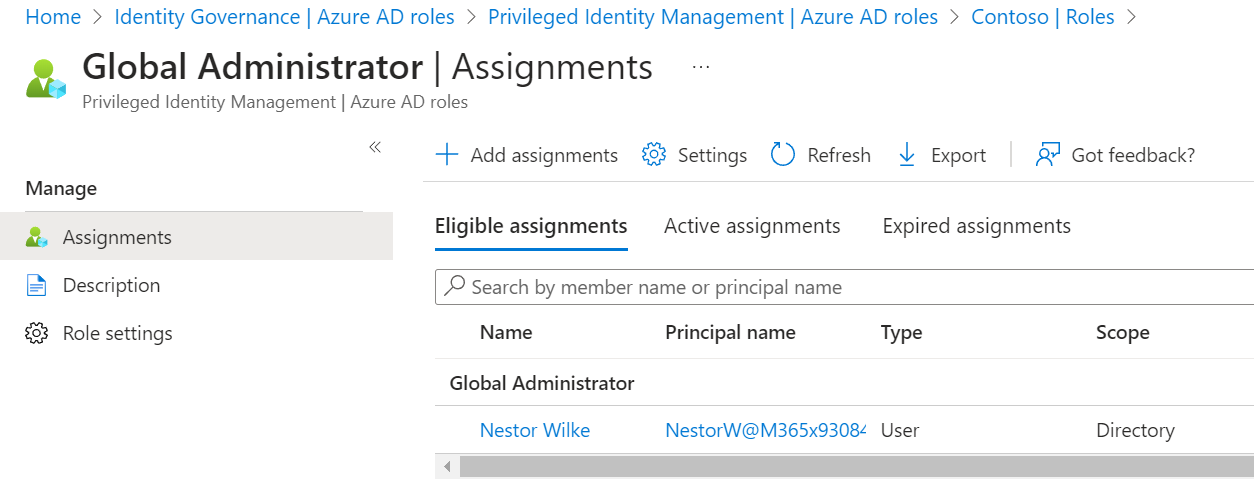
Activation of privileged roles should be monitored and require approval
Since many cyberattacks leverage privileged access, it is imperative to closely monitor the assignment and activation of the highest privileged roles for signs of compromise. Create alerts to trigger when a highly privileged role is assigned to a user and when a user activates a highly privileged role
Require approval for a user to activate a highly privileged role, such as Global Administrator. This makes it more challenging for an attacker to leverage the stolen credentials of highly privileged users and ensures that privileged access is monitored closely.
In the Configuration Manager baseline, the role settings are updated for the Global Admin role to require approval to activate the assignment. This is leveraging Microsoft Privileged Identity Management (PIM). The approvers for this activation are assigned to a group called PIM Approvers which is also created in the baseline. You will need to assign users to this group that will receive the request for approval.
