Cet article s'applique aux clients ayant rejoint CoreView avant mai 2022. Toutes les nouvelles activations utilisent notre configuration Secure By Default, où le rôle Global Admin n'est plus requis.
Cet article explique comment supprimer le rôle Global Admin du compte administrateur CoreView.
CoreView crée un compte administratif dans les comptes Microsoft 365 de nos clients pour agir en tant qu'utilisateur effectuant des activités de gestion au sein de Microsoft. En d'autres termes, un opérateur déclenchera une action de gestion telle que la modification d’un utilisateur dans CoreView, mais c'est le compte administratif CoreView qui exécutera l’action dans Microsoft. Historiquement, CoreView exigeait que ce compte soit Global Administrator afin de garantir qu'il puisse effectuer toutes les actions nécessaires.
Compte tenu de l'évolution des meilleures pratiques en matière de sécurité, CoreView reconnaît que la dépendance à un compte Administrateur global peut représenter un risque inutile. Dans notre nouvelle configuration Secure By Default, les rôles suivants sont attribués automatiquement au compte CoreView Admin :
- Global Reader
- Exchange Administrator
- Teams Administrator
- User Administrator
- Authentication Administrator
- SharePoint Administrator
Pour plus d’informations sur les rôles, veuillez consulter l’article “Attribution des rôles à l’application Graph”.
Comment modifier les autorisations pour les comptes admin existants
Pour tous les clients CoreView existants, aucun changement ne sera appliqué à votre environnement actuel. Si vous souhaitez supprimer le rôle Administrateur global de votre compte administratif CoreView, vous pouvez effectuer les étapes suivantes.
Veuillez fermer votre session de gestion avancée (si ouverte) puis vous pouvez affecter les autorisations suivantes depuis la section “Gérer les rôles d’administrateur” sur la fiche utilisateur de votre Company Administrator depuis le Microsoft 365 Admin Center :
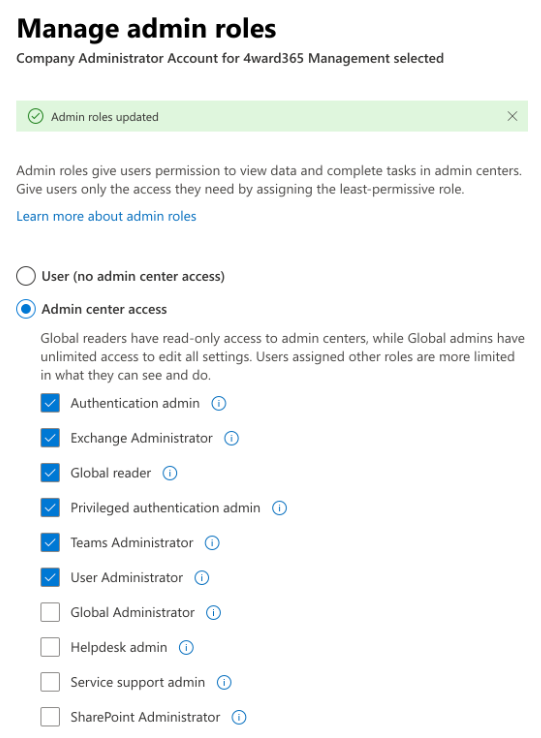
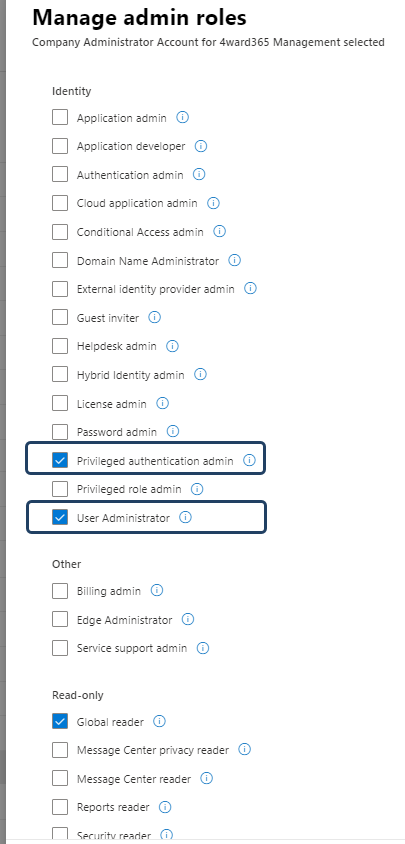
Veillez à bien retirer le rôle Global Administrator de votre liste et à affecter les rôles manquants depuis la section “Afficher tout par catégorie” :
Cliquez sur le bouton bleu “Enregistrer les modifications” après avoir modifié les autorisations attribuées.
