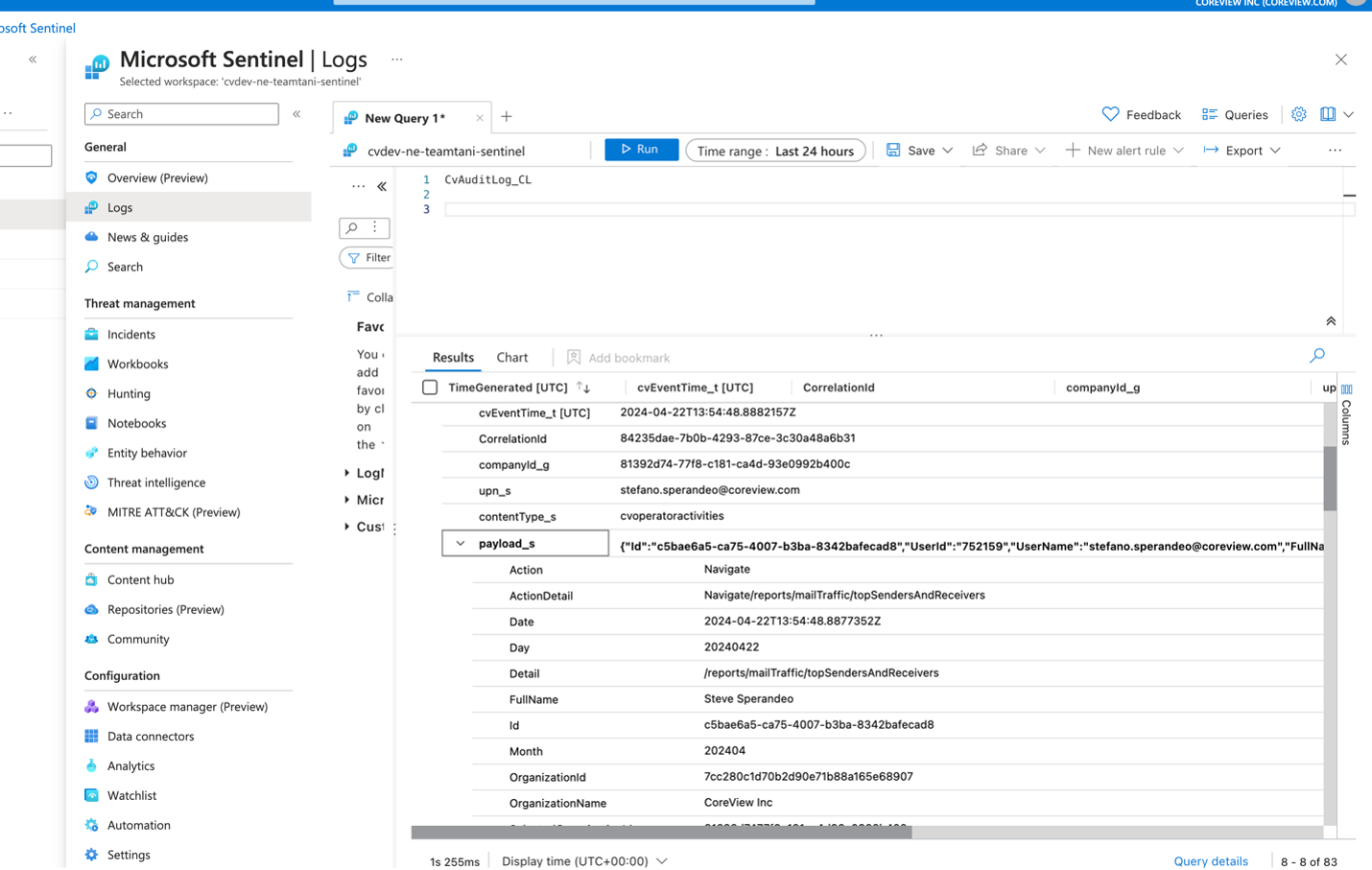
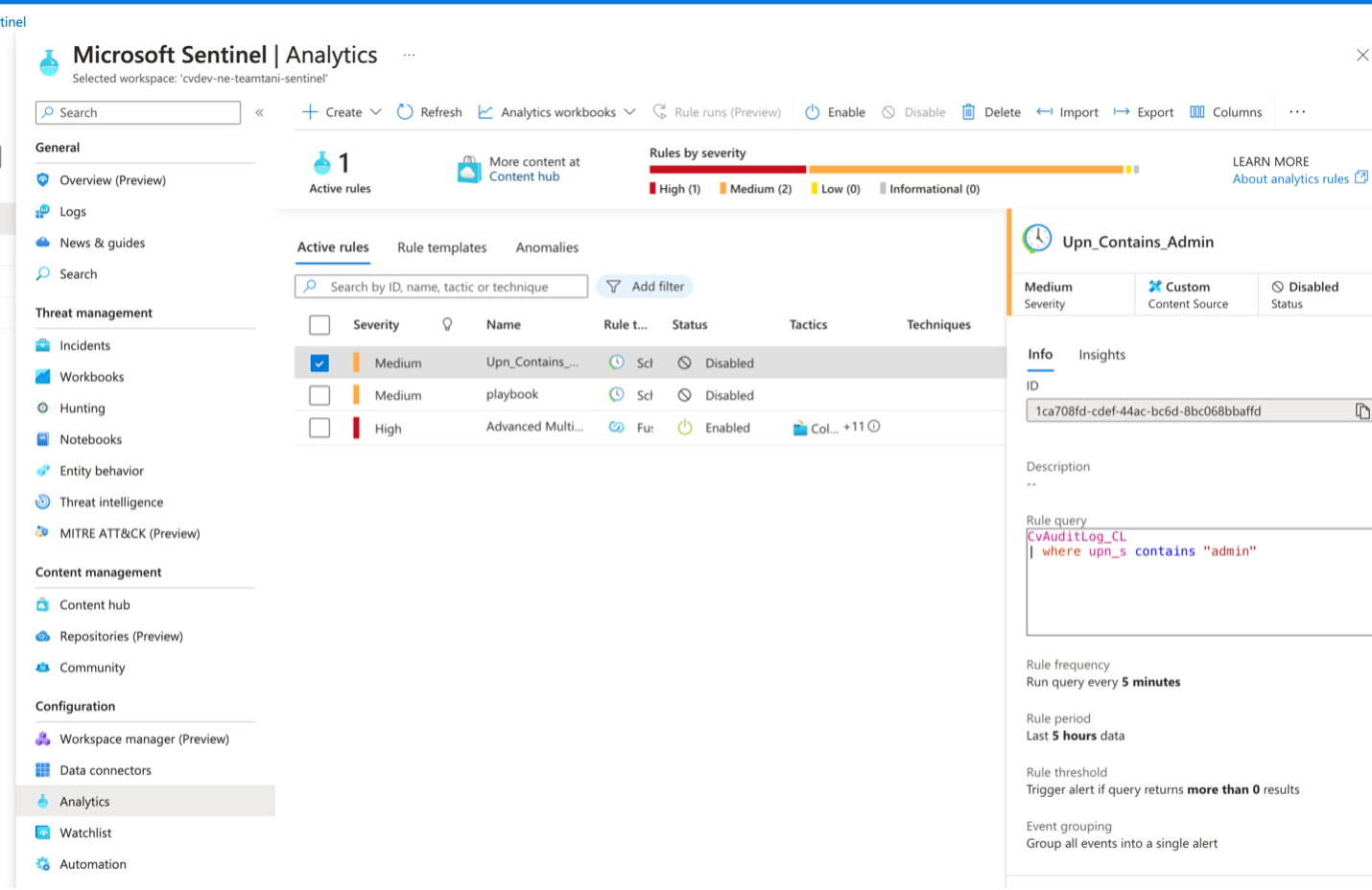
The CoreView Audit-log SIEM connector allows you to integrate all CoreView audit logs with your chosen SIEM system. These logs capture every activity and event within CoreView, as well as actions performed by CoreView operators. You will be working with logs from the CoreView Audit log report. This connector facilitates storing CoreView audit logs in an Event Hub instance on your side, enabling seamless integration with any SIEM system, including Microsoft Azure Sentinel.
Integration architecture
- Logs are automatically pushed into an Event Hub instance that belongs to you.
- The logs are then parsed and sent to your SIEM system using a Logic App.
Requirements
- Event Hub instance: you should set this up following the official Microsoft documentation.
- Logic Apps configuration guide: it is recommended to use Logic Apps for connecting the Event Hub to your SIEM system. However, this is not mandatory, and you may choose other methods if preferred.
EventHub - SIEM setup steps (using Logic Apps)
The setup involves three main steps:
- Event trigger
- Parse JSON
- Send data
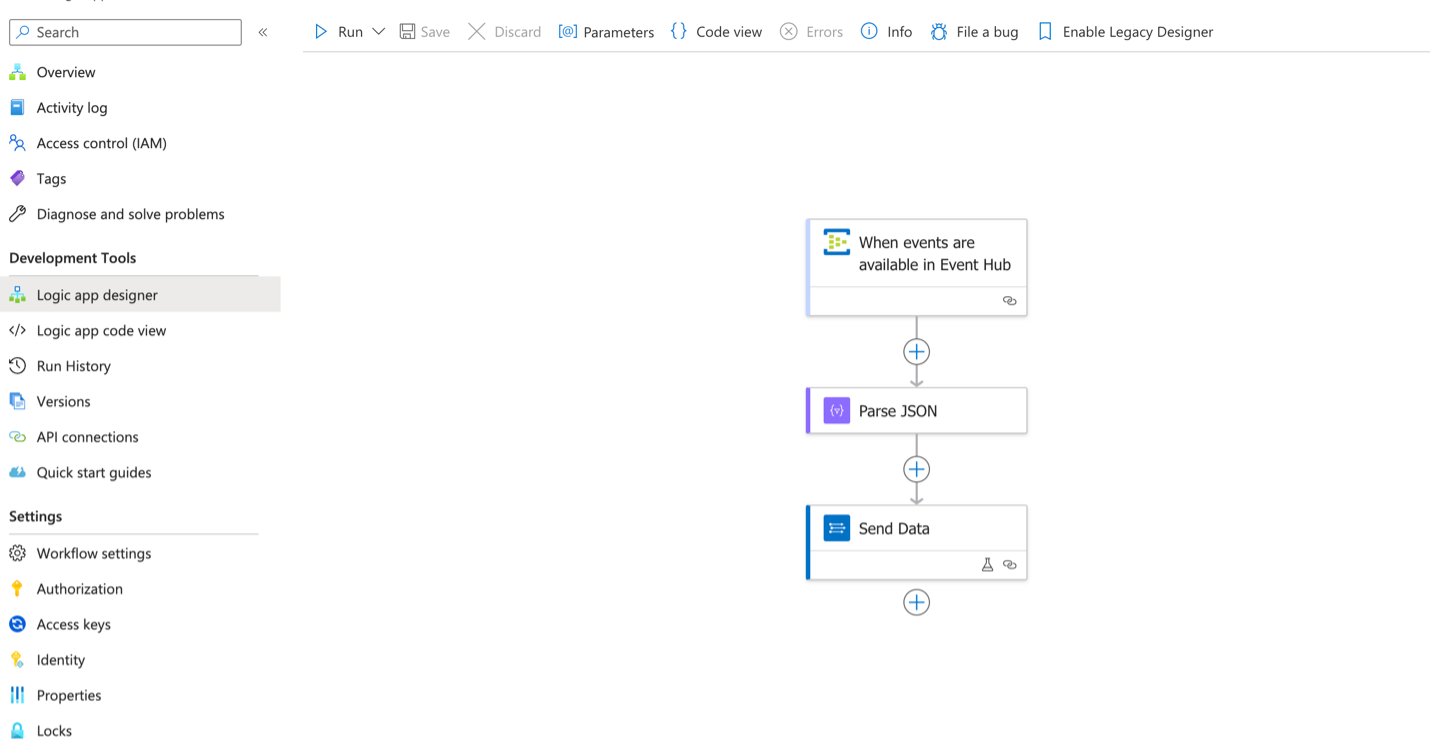
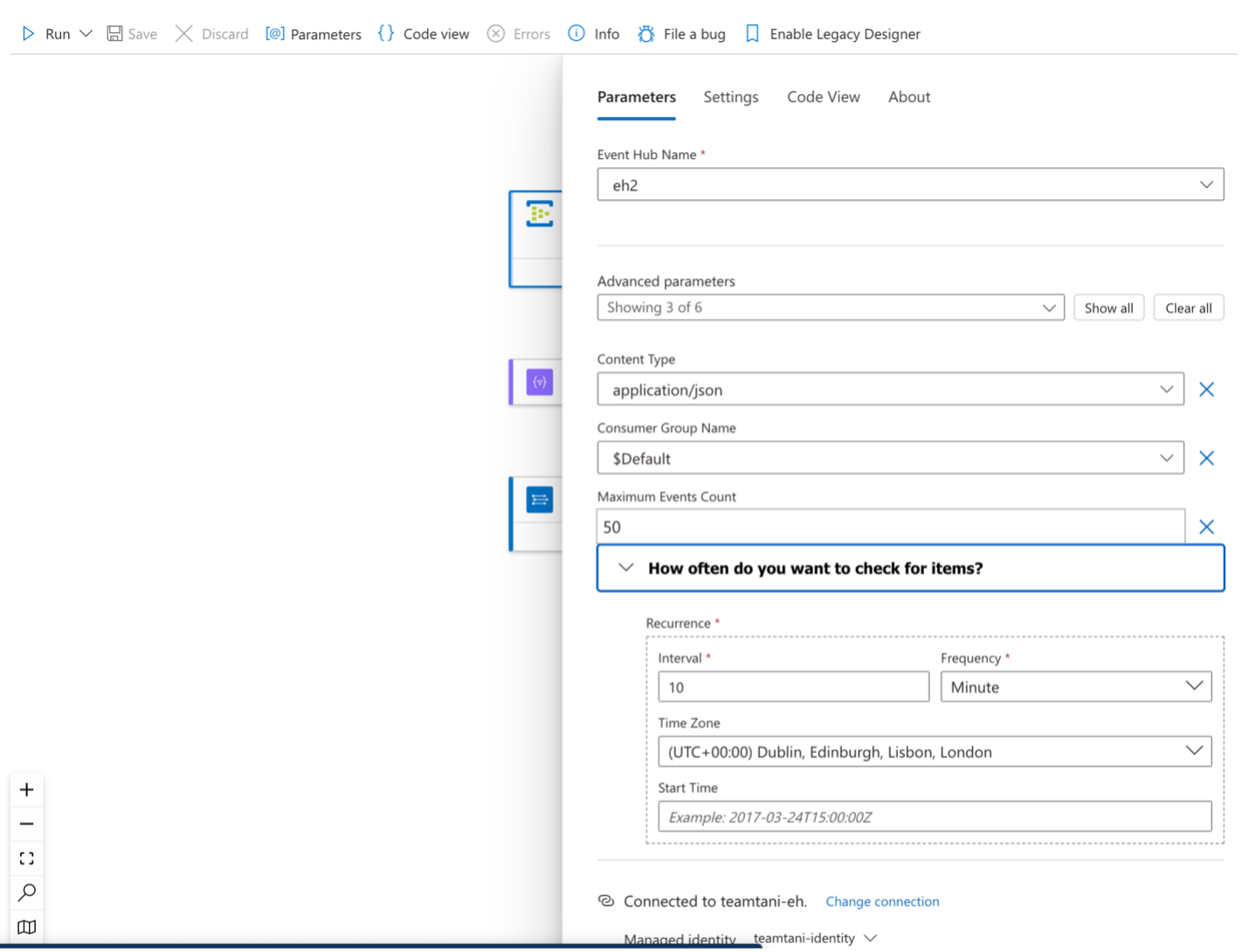
1. Event trigger
Configure a trigger to detect when events are present in the Event Hub.
2. Parse JSON
Use the following schema to parse the logs:
{3. Send data
Configure the final step to send data to your SIEM system.
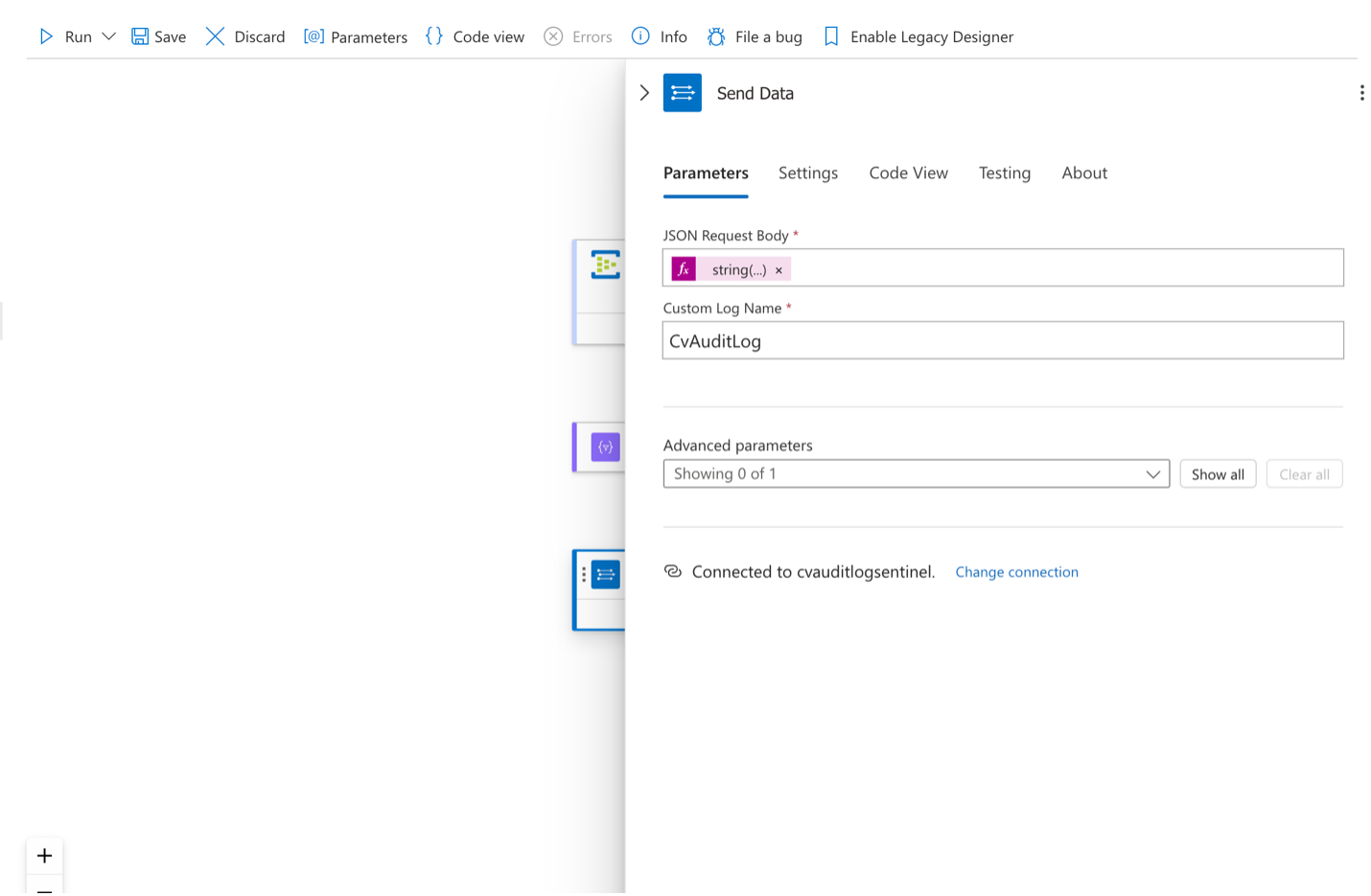
Microsoft Azure Sentinel examples