Legacy CoreView solutions
An Entra ID app connector is available for owners of legacy CoreView offerings who would like to retain access to this feature. Please contact your TAM to learn more.
This report provides a comprehensive list of apps created by your organization. It offers an overview of the high-level data for app registrations within your tenant.
Note: creation, deletion, and update events included in this report are refreshed approximately every 5–10 minutes through delta synchronization.
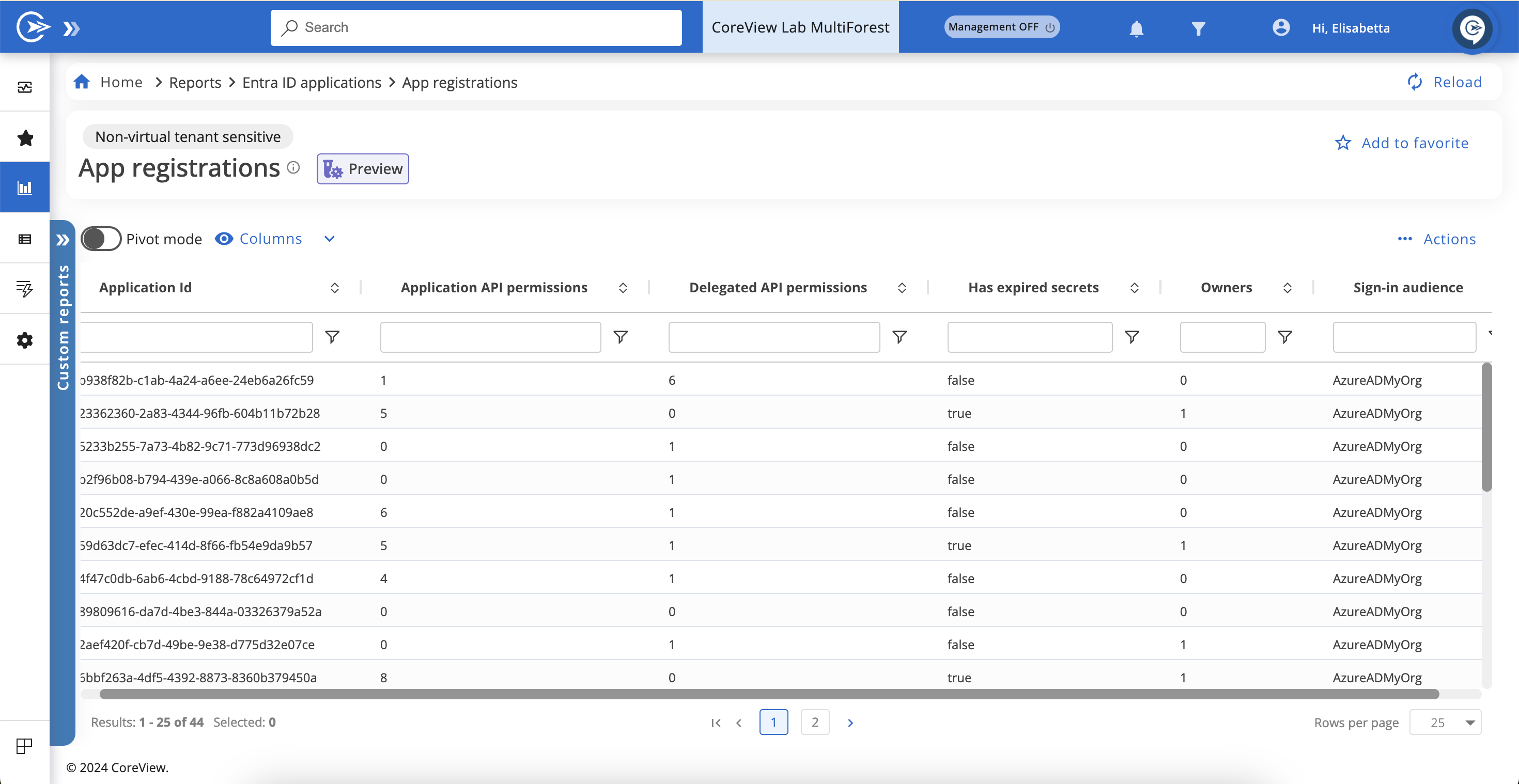
Key columns in the “App registrations” report
Display name: shows the name the app is registered under in your tenant.
Owners: displays the number of owners for each app. Clicking on this number will open the “App registration owners” report in a new page.
Delegated API permissions: shows how many permissions have been delegated to the app by either admins or users. For more detailed information, refer to the “App registration delegated permissions” report.
Application API permissions: shows the number of consents required by the app, such as requests to access a list of users or to read your mailbox. These permissions are the same as those granted through admin consent in the “Permissions” section of the Microsoft Admin Center. Detailed information is available in the “Application permissions” report.
Has expired secrets: signals whether the app's secrets have expired. For more details, consult the App secrets report.
Sign-in audience: identifies the group of users allowed to sign in and use the registered application.
Created by: displays the user who originally created the Entra App, as identified from audit log data at the time of app creation.
Note: the “Created by” column will never display the name for apps created before purchasing CoreView.
Boolean evaluation columns
The columns below, which display as true/false, assist in identifying potential issues with your app registrations:
Bad URIs: This attribute is set to True if the Web.RedirectUris array (within the Application object) includes any redirect URIs that follow these patterns: “localhost”, “http://”, “urn:”, or “*”.
Risky access: This attribute is marked as True when the AppRoleAssignment.ReadWrite.All delegated permission, considered risky, is granted.
Credentials beyond 180 days: This shows True if the credentials (either passwords or certificates) are valid for more than 180 days.
Not in use: This changes to True if the difference between today's date and the last activity date exceeds 180 days, or if there is no record of the last activity date.
